Technical Resources
Educational Resources
APM Integrated Experience
Connect with Us
Application logging is a critical part of log management and can help keep your business running smoothly and securely.
Application logging is the process of saving application events. With this information in hand, tech pros can assess threats and analyze errors before they disrupt broader business workflows.
Application logging varies from other event logs within IT systems in that the information collected by an application event log is dictated by each individual application, instead of the operating system. Knowing what to do with the wide range of data within an application log can be overwhelming, but understanding how to interpret and sift through this wealth of information will help technicians adapt to today’s rapidly evolving digital landscape.
Each application you use contains code to write different types of events to an application log file. Events within an application log file can vary, but typically include:
1. Application exceptions
2. Major events like startups, stops, restarts, and security events
3. Error event notifications
4. Debug information
5. SQL logs
6. Warnings about low disk space
These events are classified as error, warning, or information, depending on the severity of the event, and often come equipped with a time stamp. With application log management software, you can set alert thresholds and receive instant updates if an event has crossed your predetermined threshold, making it easier to navigate the volumes of event data. These application logging tools even let you know the problem area within the application, so you can take a swift course of action.
Upholding the safety, security, and efficiency of the many applications your colleagues rely on daily is paramount to your company’s success. Follow these top ten application logging best practices to help ensure you never miss a thing.
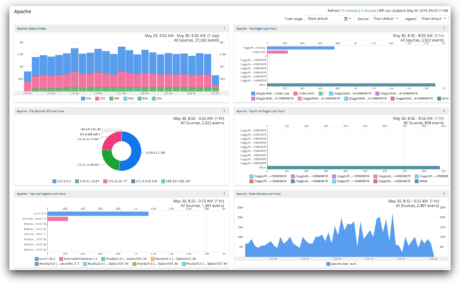
Just because something can be logged, doesn’t mean it should be. Spend some time getting to know what type of information your applications are logging, and determine what’s relevant to your business. This will not only save you a tremendous amount of time, but could also save your business from having to put extra resources behind storage space to house unnecessary data.
Sorting through the thousands of lines of raw data within an application log is no easy task. With third-party application logging tools, you can dictate which information your applications should forward to the software. This allows you to focus on critical issues at hand, instead of being bogged down by every bit of activity. These application log monitoring tools will even automate many of the tedious tasks, like parsing, involved in the application log management process.
Put all application and network device log data into a central, accessible location. This will take the headache out of managing countless event logs and help you achieve a more holistic view of your network infrastructure. An aggregated system also makes sharing data and producing comprehensive reports easier, so you can remain compliant with all relevant industry standards.
Leverage an application log management tool syncing with your messaging system (Slack, HipChat, etc.), so your team can get instant alerts when a suspicious event has occurred. Many tools on the market also offer interactive dashboards, customized to feature complex datasets and time-based dimensions. These dashboards can then be shared via a link to other members of your team, who can edit the dashboard based on the permission level you’ve set.
An application event log can include some sensitive information. If you’re using a third-party log management platform to aggregate your data and implement an alert system, make sure it’s following all relevant industry security standards. Encrypting sensitive data logs before sending them is also a must.
Each application produces a high volume of event data. The more applications you have, the greater the volume you’ll need to manage. Designating a storage limit or rotation policy is paramount to successful application log management. You can do this through the configuration settings within your local storage policies or by setting up disk-assisted queues. Without any storage system in place, you run the risk of losing recent log data, which can’t be saved if the log file is at capacity.
Alerts are great because they let you know in real time when your event threshold has been crossed. But relying on alerts alone won’t cut it—take a proactive approach and frequently review your logs. A well-maintained, centralized log can help you identify recurring issues, evaluate the source of these issues, and stay abreast of any anomalies.
Many cybercriminals will try to access log files and delete any evidence of their activity. Record logs both locally and to a remote storage site which will be harder for criminals to access. Discrepancy between the two files can trigger an alarm and prevent a breach from going unnoticed.
Application logging tools often offer a robust search function, allowing you to analyze the activity leading up to and following an event, so you can better determine its root cause. Access to this type of interactive data is essential to the overall health of your system.
No two businesses are alike. The information you need to gather and analyze from your application event log is unique, and the way you use your application log monitoring tool should be too. Create custom parsing rules, select which application event log data is most pertinent to your company, and leverage color coding to focus only on areas of interest.
Application logging tools can play a vital part in any tech pro’s strategy, regardless of your company’s size. With the right software, you can streamline tedious processes, narrow down large volumes of data, and receive real-time alerts of suspicious activity. These extensive capabilities can give you hours back in your day and help protect your company’s overall IT health.
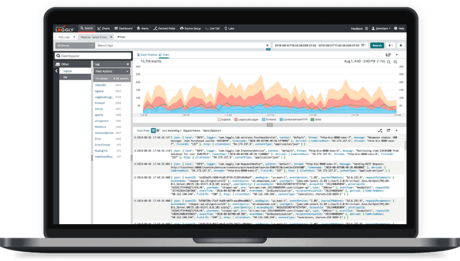
When sifting through the many application log management tools on the market, look for something robust and reliable. SolarWinds® Loggly® is a comprehensive tool uniting all of your event log data into one easy-to-access hub. The platform boasts interactive dashboards and dynamic search functions to help you rapidly pinpoint discrepancies within application event activity and identify the source of an issue. Loggly also takes all security best practices into consideration, leveraging encryption protocols and authenticated login credentials to keep your data safe and secure. Visit our product page today and find out if Loggly is the right tool for your business.